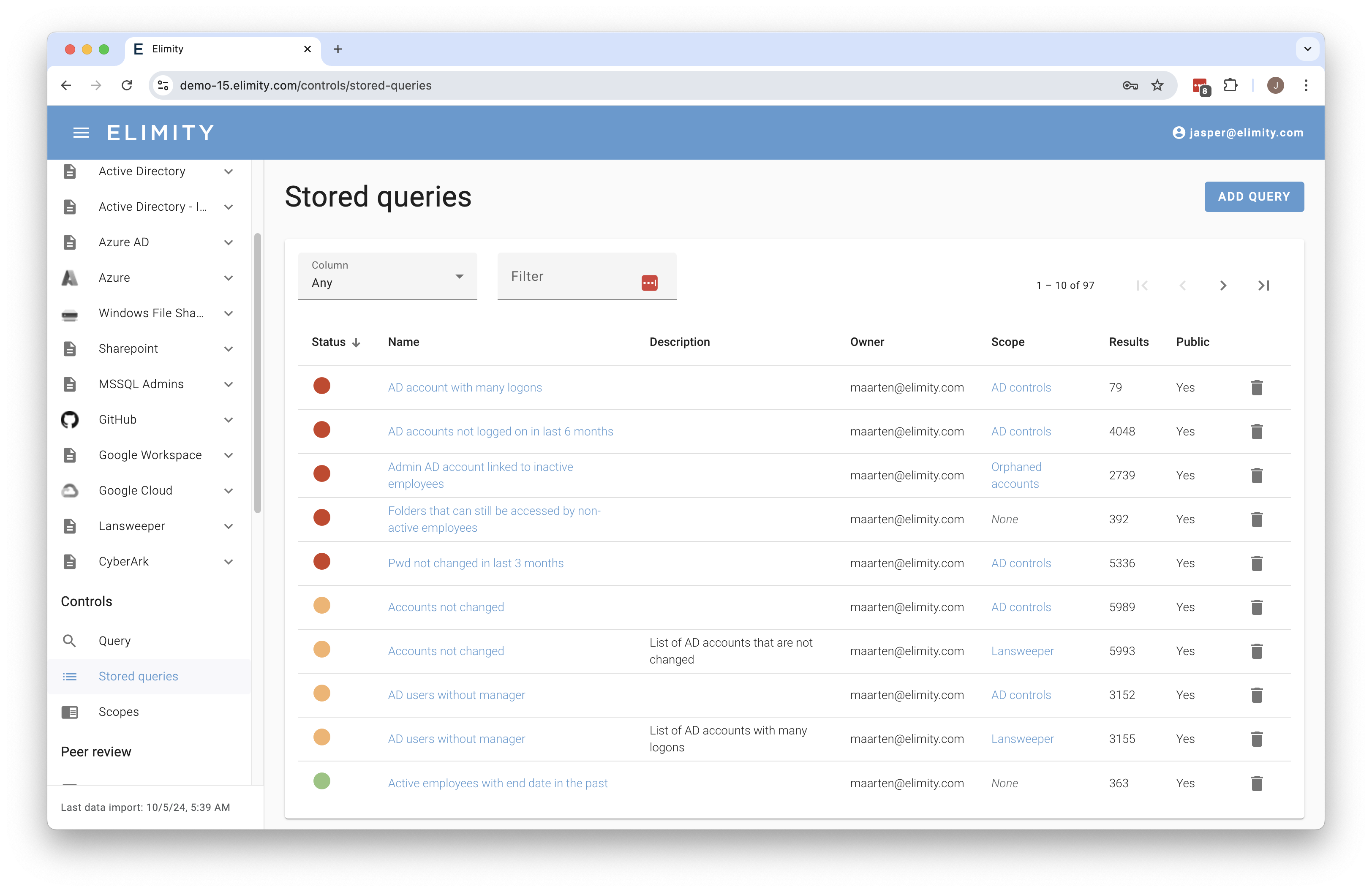
Prove that you are in control of who can access what
Description
“Who can access what within my organization?”
Elimity enables organizations to answer this crucial question within days—not months.
With provable control over user access being essential for NIS2 and ISO27001 compliance, Elimity offers the fastest way to gain full visibility into users and their access rights across your IT landscape.
Our lightweight platform, Elimity Insights, empowers security teams to:
- Understand who can access what
- Identify and clean up risks
- Automate access reviews
- Monitor access continuously
No complex implementation or heavy IGA suite required.
Vendor properties
-
100%
0%
Vendor details
- Market indipendent/agnostic (Means the solution overlaps all markets, and is linked to all)
 Danish
Danish
 Dutch
Dutch
 English
English
 Finnish
Finnish
 French
French
 German
German
 Norwegian
Norwegian
 Swedish
Swedish
The vendor did not specify this data field

 Belgium
Belgium